Petya cyber attack outbreaks and keeps spreading worldwide as the aftermath of WannaCry ransomware, the Petya ransomware, crippled many critical systems globally, from Danish shipping conglomerate to Merck, the drug giant in the United States and Ukraine’s government system, even the premier’s computer.
How Does the Petya Ransomware Work?
Petya ransomware, also known as Petrwrap, NotPetya, or GoldenEye, wreaks the computer with the built-in EternalBlue exploit code through phishing emails or scams. Once assaulted by Petya virus, the system’s Master Boot Record (MBR) section will be altered and then Petya virus code will take over of the computer ahead of the Windows when reboots, showing a fake disk check process for the Master File Table (MFT) where the GoldenEye executes the files encrypting on most Windows operating systems, especially Windows 7, Windows Vista, Windows XP and the predecessors.
When the machine completes the reboot, the encryption havoc on the MFT section finishes at the same time. You will then be asking for and 300 bitcoins ransom to recover the locked files and information.

How to Enable the Petya Ransomware Vaccine for Windows PC?
If you are looking for Petya vaccine or Petya wiper to prevent your Windows computer from the Petya cyber ransomware attacking, below are top 5 prevention tips keep your desktop or laptop away from the malware.
Method 1. Be Vigilant to the Suspicious Links
Since the main spreading channel of the Petya ransomware is phishing e-mail, you should be highly vigilant to the suspicious emails and then perform below basic tips for security.
• Avoiding clicking any suspicious emails and links.
• Turn on the Windows updates to ensure the latest Windows security patches can be installed timely.
• Update your Antivirus programs regularly for the enhanced security.
• Ensure you have enabled User Access Control on the endpoint and consider operating as a standard user and not a user with administrative privileges
• Backup your important information regularly with the external tools, like the cloud backup, UBS flash drives or online storage provider (DropBox, Google Drive and Microsoft OneDrive etc.).
Those are the very basic but essential steps you could do to avoid NotPetya’s attack.
Method 2. Install the Windows Security Patch to Prevent the Petya Ransomware
It is crucial to deploy the latest Microsoft patches, Microsoft Security Bulletin MS17-010, the same vaccine for WannaCry ransomware, which patches the SMB vulnerability. Microsoft has published the related tutorial post on the new ransomware, Petya, you can have a look from there to see what they are doing to prevent the spread of this ransomware. Below are the download links of MS17-010 patches.

• Patch for Windows XP and WindowsServer2003/English language security updates:
• Patch for Windows 7:
https://technet.microsoft.com/zh-cn/library/security/MS17-010.aspx
See Also:How to Enter Safe Mode in Windows 10, 8.1, 8, 7, Vista, XP
Method 3. Disable SMBv1 Protocol to Avoid Petya Cyber Attack
Apart from installing the MS17-010 patches, disabling the SMBv1 protocol consists also functions as the Petya wiper since the Petya virus could exploit NSA-built Windows exploit known as “Eternal Blue” which targets the SMBv1 protocol via the Microsoft's CVE-2017-0199 vulnerability. And SMBv1 protocol is available on the following Microsoft operating systems:
• Windows XP (all services pack) (x86) (x64)
• Windows Server 2003 SP0 (x86)
• Windows Server 2003 SP1/SP2 (x86)
• Windows Server 2003 (x64)
• Windows Vista (x86) (x64)
• Windows Server 2008 (x86)
• Windows Server 2008 R2 (x86) (x64)
• Windows 7 (all services pack) (x86) (x64)
To disable SMBv1, you can run the following commands in Power Shell on each system or you can refer to the Microsoft detail instructions of how to disable SMBv1 in Windows.
• Check for SMBv1:
Get-SmbServerConfiguration | Select EnableSMB1Protocol
• Disable SMBv1 on the SMB server:
Set-SmbServerConfiguration -EnableSMB1Protocol $false
Method 3. Restrict Administrator Privileges
The malware requires administrator rights to the local computer. Standard users should not have this in permission. Consider restricting who has local admin rights to prevent the execution of exploit code within organizations. Home users should also consider using a Standard User Account for day-to-day operations.
Method 4. Create a Read-Only File Named C:\Windows\perfc
To vaccinate your Windows computer from the Petya attack, like WannaCry, Petya also has its own KillSwitch Dutch, creating a read-only file named C:\Windows\perfc, which helps you to stay away from the infection of the current Petya virus. Below is how.
1. Open the Command prompt with administrator rights.
2. Type cd.. and then hit Enter.

3. Type copy on perfc and then hit Enter.
4. Press Ctrl + Z and then hit Enter.
5. Type copy on perfc perfc.dll and then hit Enter.
6. Type copy on perfc perfc.dat and then hit Enter.
Method 5. Create a System Restore Point to Backup Important Data
Remember to backup your important information, say your documents, hardware device drivers, applications, etc. for your Windows PC. You can backup all those data with a system restore point. Driver Talent, a trustworthy drivers and Windows OS backup utility, could help you to do so.
Click the button above to get Driver Talent and follow the 3 steps to create a system restore point.
Launch Driver Talent and turn to the Backup menu.
2. Select Restore menu and select System Restore.
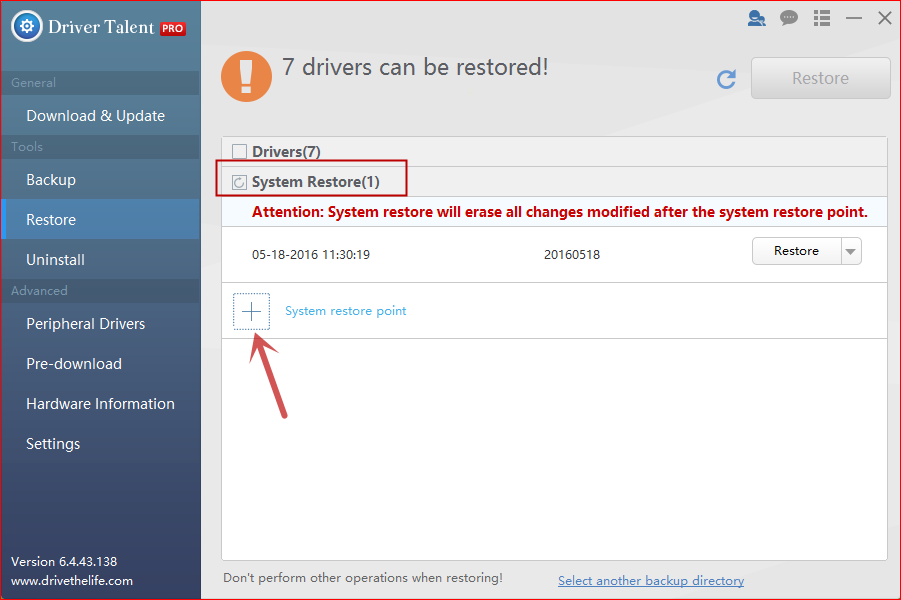
3. Click System restore point to name the point.
4. Click Create to perform the system restore point.
That’s all! We will update this post if more workarounds are found to prevent your Windows laptop or desktop from Petya ransomware attack. Comment below to share with us if you find other brilliant solutions on avoiding Petya Cyber attack or go the OStoto official forum to discuss with us.
You may also like to check out:
• How to Avoid Ransomware Attacking Your Windows, iOS or Android Device









